Building a VPN appliance for network-wide routing using advanced DHCP settings
Self-hosting applications behind a VPN is great for simplicity and security. However, applying the VPN configuration to every single device on a remote network quickly becomes cumbersome. Instead, I wanted something to allow servers on the corporate network to be reachable across the whole home network from a single configuration point.
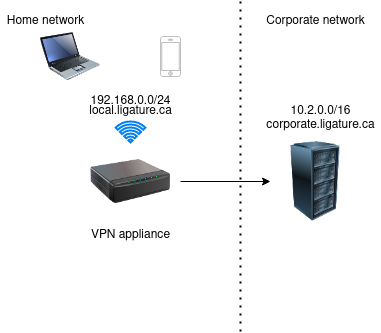
Remote site network architecture
Using a set of advanced DHCP options, it is possible to provide
additional static routes to every client for the VPN, while still preferring
the default ISP route for everything else. The relevant DHCP options
are router(3), dns-server(6) and static-routes (121).
The router (3) option specifies the default route for traffic. Since the DHCP server is hosted on a separate machine, we have to manually specify it to point to the ISP router.
The dns-server (6) option indicates that the separate DHCP server should be queried regarding any DNS request. This allows us to easily bypass the ISP router to use our own rules.
Finally, the static-routes (121) option specifies static routes that clients should use, by order of preference. In our case, we should route requests to 10.2.0.0/16 through the DHCP/VPN server (192.168.0.2) and everything else (0.0.0.0) through the default ISP router (192.168.0.1). This is crucial to keep the regular traffic from being forced through the VPN link, which would result in increased latency.
Here are the rules in dnsmasq.conf format.
server=/corporate.ligature.ca/10.2.0.2 # Upstream DNS server for the corporate network
dhcp-option=option:router,192.168.0.1 # The real router (ISP) is at 192.168.0.1
dhcp-option=option:dns-server,192.168.0.2 # *I* am the DNS server for this network
dhcp-option=121,10.2.0.0/16,192.168.0.2,0.0.0.0/0,192.168.0.1 # Route 10.2.0.0/16 through 192.168.0.2, everything else through 192.168.0.1
See also the full dnsmasq.conf.